Login aplikasi lebih aman dengan autentikasi real-time


Autentikasi dapat berjalan secara otomatis tanpa memerlukan tindakan dari pengguna.

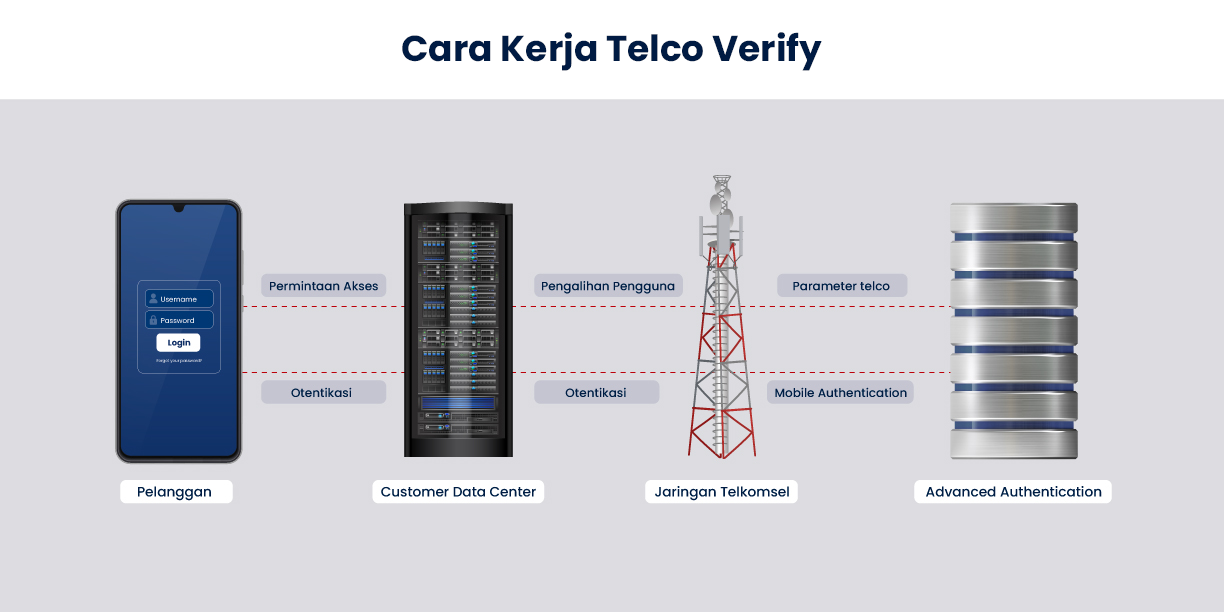
Pengembangan menjadi efisien karena proses autentikasi terjadi melalui carrier network.

Meminimalisir risiko penyerangan cyber dan pengambilalihan akun bagi pengguna.

Memberikan kemungkinan untuk integrasi dengan solusi autentikasi lainnya.
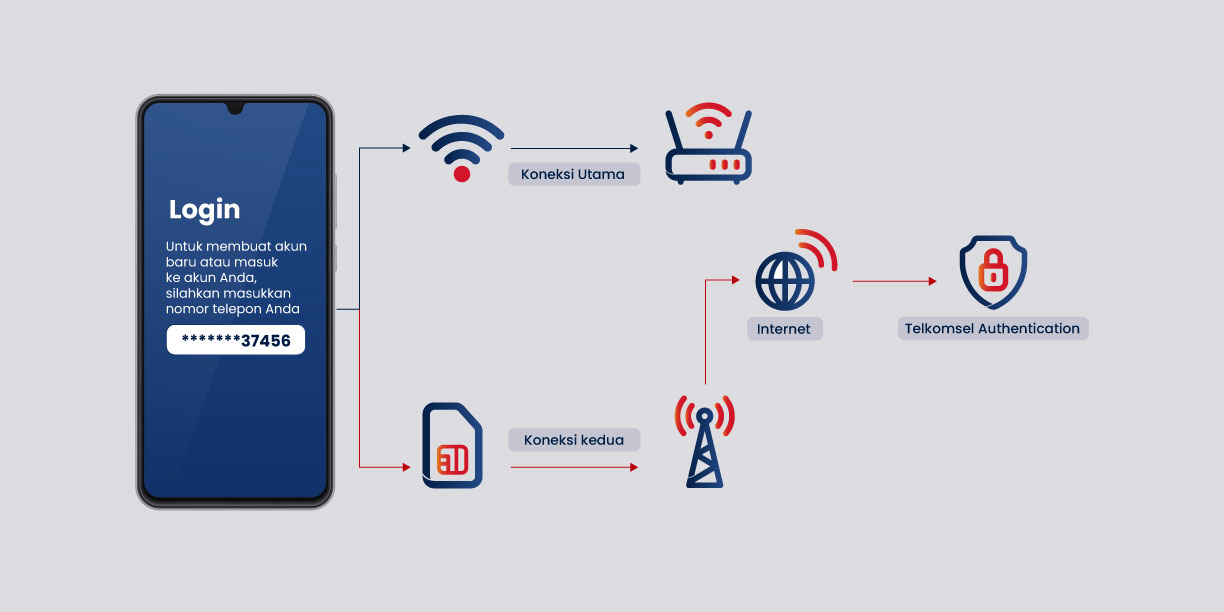
Metode ini tetap dapat digunakan dengan baik saat terhubung melalui WiFi maupun menggunakan operator seluler selain Telkomsel.
Mayoritas cenderung menggunakan mobile (ponsel), tapi tidak menutup kemungkinan dapat menggunakan media lain seperti QR code.
Koneksi akan secara otomatis beralih ke jaringan seluler untuk proses autentikasi. Sehingga, proses autentikasi tetap berjalan saat pengguna dialihkan ke jaringan WiFi.
Metode ini tidak melibatkan pengguna untuk mengakses URL. Berbeda dengan metode OTP yang memerlukan keterlibatan pengguna dalam memasukan kode. Solusi ini secara langsung akan mengautentikasi URL yang diberikan.
Pengguna diharuskan untuk memiliki paket data atau pulsa agar dapat diverifikasi pada jaringan seluler.
Telco Verify merupakan solusi autentikasi dengan teknologi terbaru yang aman dari ancaman serangan cyber karena pengguna tidak perlu menginput kode verifikasi apapun pada aplikasi.

Sampaikan kebutuhan bisnis Anda

Kami akan merancang solusi sesuai kebutuhan Anda dan memberikan trial

Membuat perjanjian kerja sama untuk implementasi solusi secara komersial

Solusi diimplementasikan ke aplikasi Anda.

Mobile Endpoint Protection
Atasi ancaman & analisis virus pada perangkat, yang dilengkapi Machine Learning.
Mobile Device Management
Menjaga keamanan perangkat karyawan yang dapat diakses kapan saja.

Telkomsel Guard
Aplikasi perlindungan perangkat dari serangan siber dengan Machine Learning.

Network Security
Melindungi jaringan perusahaan tanpa mengurangi performa lewat premis Telkomsel.